Introduction to FIDO2 Authentication in WSL #
Windows Subsystem for Linux (WSL2) provides a powerful Linux environment directly within Windows, eliminating the need for dual-booting or virtual machines. Despite its advantages, WSL has limitations regarding USB device access, posing challenges for hardware security token implementation.
As a cybersecurity engineer specializing in incident response and security automation, my workflow spans Linux, Windows, and macOS environments while requiring secure access to SSH and GIT resources. After experiencing challenges with the traditional OpenPGP interface on Yubikeys—including complex configuration and stability issues—I’ve identified FIDO2 as a superior alternative for both SSH authentication and GIT commit signing.
This guide demonstrates how to configure WSL to utilize the FIDO2 interface on Yubikeys through the Windows host system, avoiding unstable USB forwarding methods.
Technical Requirements #
This implementation references three SSH environments:
- Windows SSH Client
- WSL (Linux) SSH Client
- Remote SSH Server
⚠️ Prerequisite: This guide assumes you have already enabled the FIDO2 interface and generated appropriate keys with your Yubikey device.
Implementation Procedure #
1. Version Requirements #
Ensure all SSH implementations (Windows, WSL, Remote) are running OpenSSH 8.3 or higher, which introduced FIDO2 support.
2. Windows SSH Client Configuration #
Update the Windows SSH client using one of these official sources:
3. WSL SSH Client Update #
Upgrade your SSH client in WSL using either:
Option A: Build from source
wget https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-9.5p1.tar.gz
tar -xzf openssh-9.5p1.tar.gz
cd openssh-9.5p1
./configure && make && sudo make install
Option B: Install via Homebrew
# Install Homebrew first if needed
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
# Install OpenSSH
brew install openssh
4. Configure SSH Helper for Hardware Access #
Add the following environment variable to enable Yubikey access from WSL through the Windows host. Add this to your shell configuration file (~/.bashrc, ~/.zshrc, or /etc/profile):
export SSH_SK_HELPER="/mnt/c/Program Files/OpenSSH/ssh-sk-helper.exe"
Source the configuration file or restart your terminal to apply changes:
source ~/.bashrc # Or appropriate config file
5. SSH Key Configuration #
Ensure your FIDO2-generated keys are properly configured:
- Verify keys exist in
~/.ssh/directory - Set appropriate permissions:
chmod 700 ~/.ssh chmod 600 ~/.ssh/id_* chmod 644 ~/.ssh/*.pub
6. GIT Configuration for SSH Signing #
Configure GIT to use SSH for commit signing:
git config --global gpg.format ssh
7. Specify SSH Signing Key #
Configure your specific SSH key for GIT operations:
git config --global user.signingKey ~/.ssh/id_ed25519_sk
8. Implementation Testing #
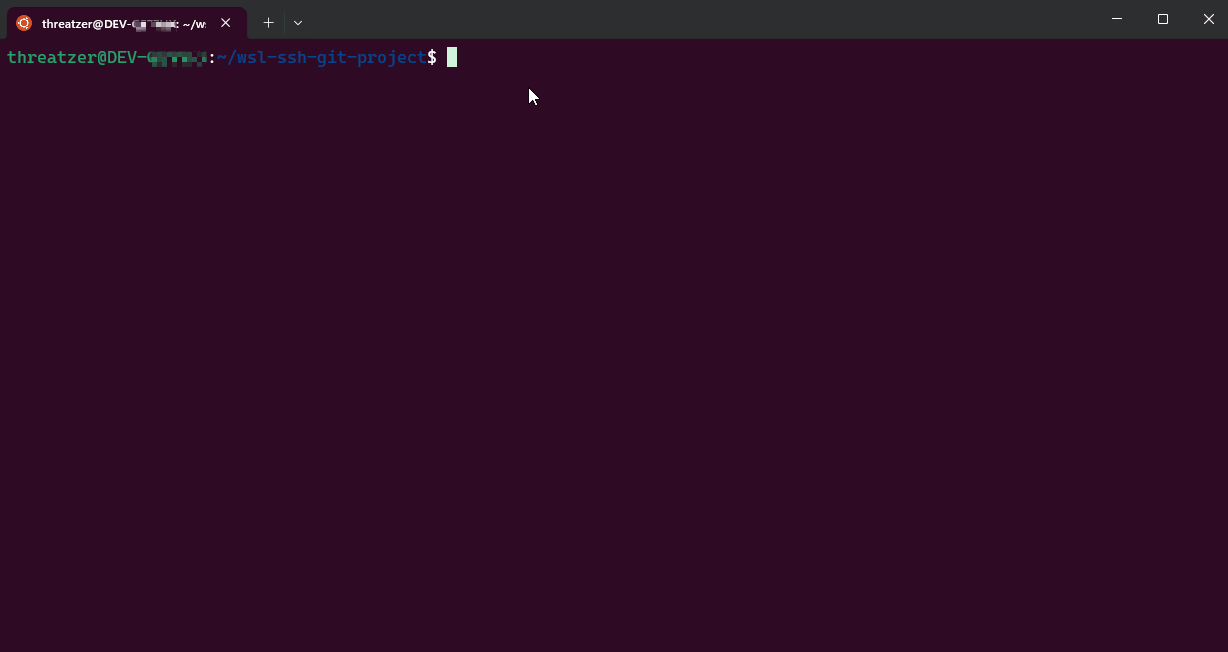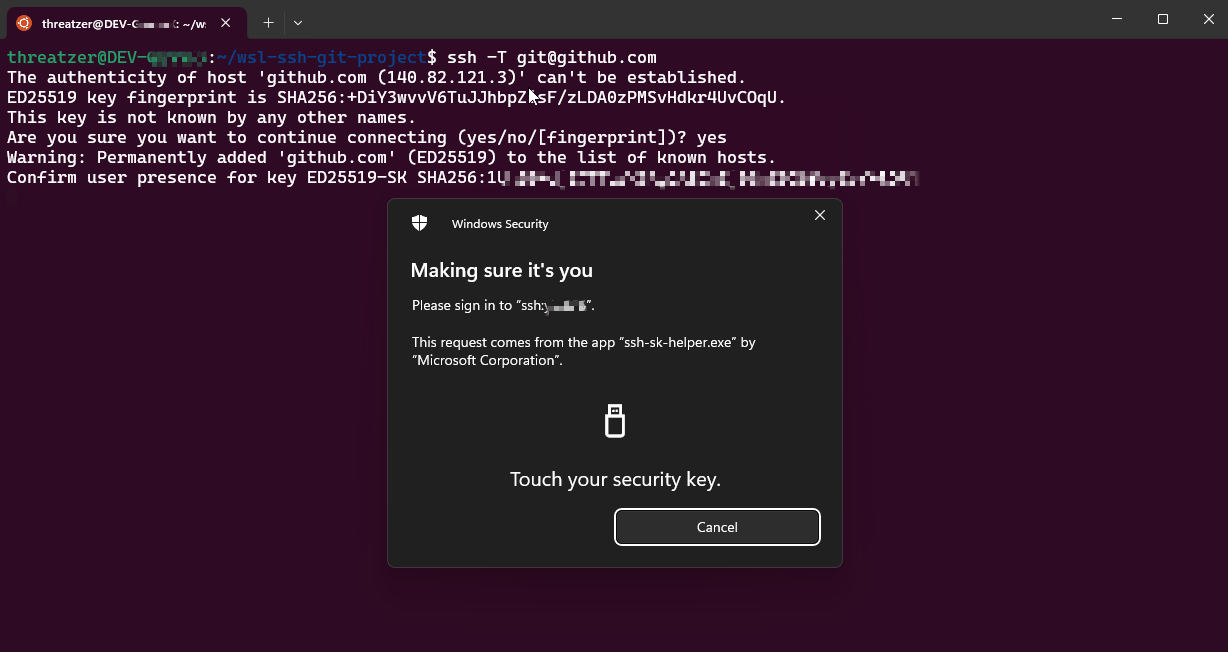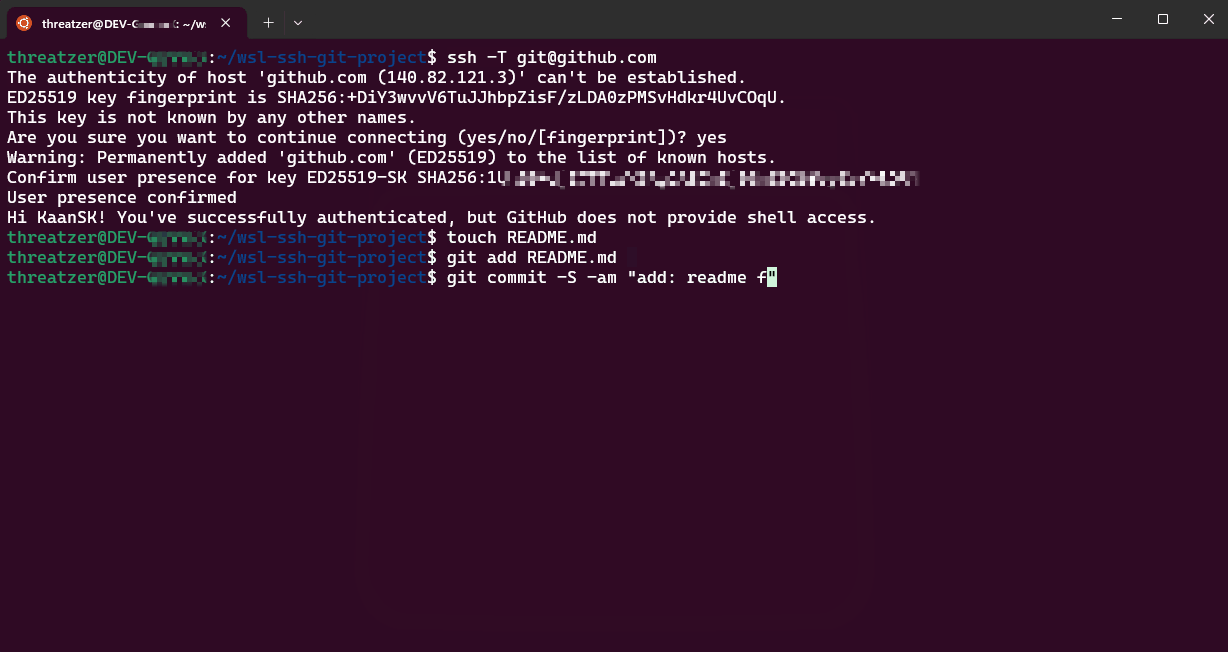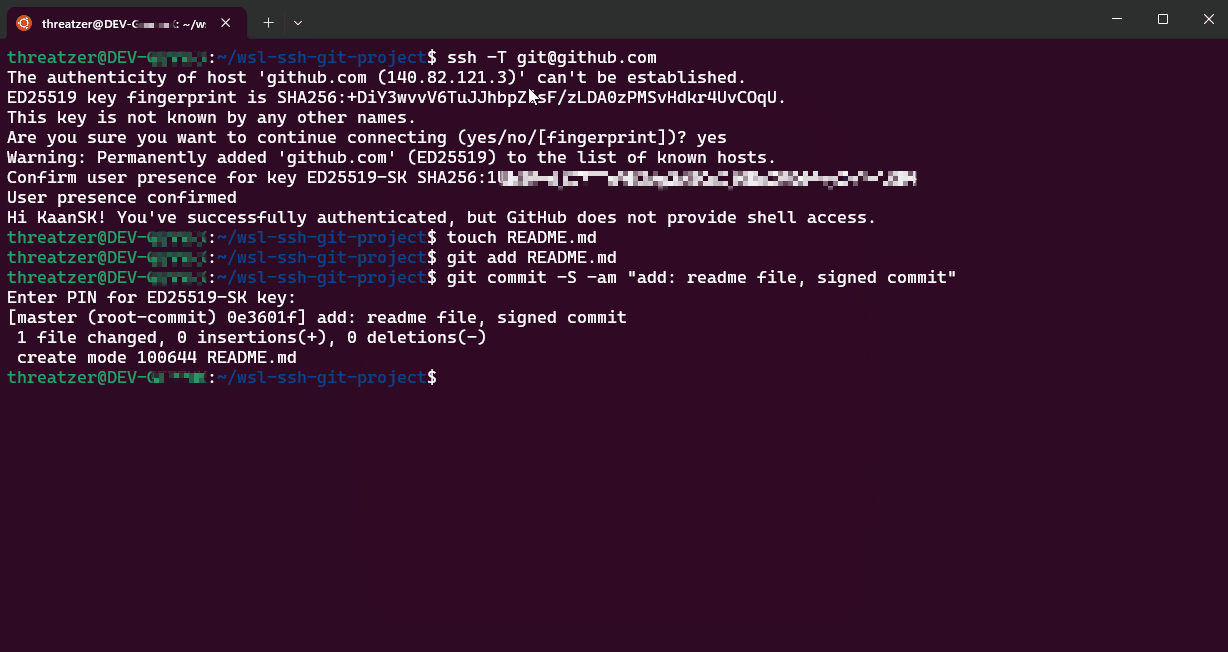
Validate your configuration by connecting to a server with your public key configured:
Security Considerations #
- The FIDO2 security model provides strong protection against phishing attacks through origin binding
- Physical presence verification (touching the Yubikey) ensures authentication cannot be automated by malware
- Keys remain protected by the hardware security element, never leaving the Yubikey device
Conclusion #
This configuration enables secure SSH authentication and GIT operations directly from WSL using Windows-connected Yubikeys without unstable USB forwarding solutions. The implementation leverages the FIDO2 protocol’s security advantages while maintaining the productivity benefits of the WSL environment.
By configuring the environment variable to use Windows’ SSH helper with WSL’s SSH client, we achieve seamless hardware security token integration across the Windows/Linux boundary.
References #
- Yubico: Securing SSH with FIDO2
- Yubico: Securing GIT with SSH and FIDO2
- Microsoft: USB device connectivity in WSL
- OpenSSH Release Notes
Note: Hero image generated by Microsoft Copilot
